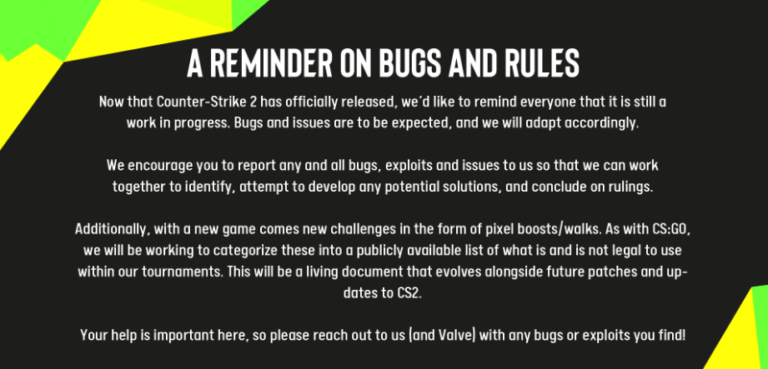
The gaming community has recently been abuzz with alarming reports surrounding a potential security loophole in CS2. One that could significantly compromise players’ safety within the game. While the details are still evolving, it’s essential to take precautionary measures until the issue is effectively addressed by Valve.
What’s the Concern?
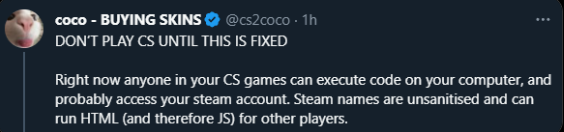
A purported exploit within CS2 has been hinted at. It suggests that the manipulation of HTML code within Steam names might lead to cross-site scripting (XSS) vulnerabilities. Such vulnerabilities could enable unauthorized access to sensitive information or, in worst-case scenarios, lead to malicious activities.

Reports have surfaced claiming that utilizing HTML in one’s Steam name could result in various security breaches. Allegedly, an individual could embed an IP grabber or an IP logger within their Steam name. This enables them to gather the IP addresses of all players sharing the same server. While this is disturbing on its own, it’s further speculated that these vulnerabilities might extend beyond IP harvesting, potentially allowing more invasive actions like running code on users’ computers or even compromising their Steam accounts.

Verification and Authenticity
The gaming community has been divided over the validity of these claims. A blurred image has circulated on Reddit, purportedly showcasing someone using this exploit to gather IP addresses. Yet, it’s vital to be cautious, avoiding hasty assumptions solely from unconfirmed visual evidence.
It’s essential to remember that speculation can sometimes outpace reality, leading to unnecessary panic. While the severity of the situation cannot be understated, it’s equally important not to amplify unconfirmed information without concrete evidence.
Valve’s Response
At the time of writing, Valve, the company behind CS2, has yet to officially acknowledge or address these reported vulnerabilities. However, given the gravity of the situation, it’s reasonable to assume that they are actively investigating the matter and working on a swift resolution to mitigate any potential risks to players.
Immediate Steps for Players
In the wake of these reports, it’s strongly advised for CS2 players to exercise prudence:
- Avoid HTML in Steam Names: Until a confirmed fix is implemented, refraining from using HTML code in Steam names might mitigate potential risks.
- Monitor Updates: Keep an eye out for official communications or updates from Valve regarding this matter. Timely updates or patches from the developers should be applied immediately upon release.
- Report Suspicious Activity: If you notice anything unusual or potentially harmful while playing CS2, such as strange behavior, unexpected pop-ups, or suspicious links, report it to Valve and exercise caution.
- Stay Informed: Rely on verified sources and official statements from Valve or reputable tech/security experts for accurate and up-to-date information on the situation.
Please Stay Safe!
While the details surrounding the reported security exploit in CS2 remain somewhat murky, the potential risks associated with these vulnerabilities cannot be overlooked. Maintaining a vigilant approach, avoiding potential risk factors, and staying informed through credible sources are crucial until a confirmed resolution is provided by Valve.
Ensuring player safety is crucial; swift action from gaming firms to address vulnerabilities is essential. Hoping for Valve’s effective response to fortify CS2’s security.
Remember, while caution is warranted, responsible reporting and avoiding sensationalized claims are equally important to prevent unnecessary panic within the gaming community.
Stay safe, stay informed, and let’s await further developments on this pressing issue within CS2.